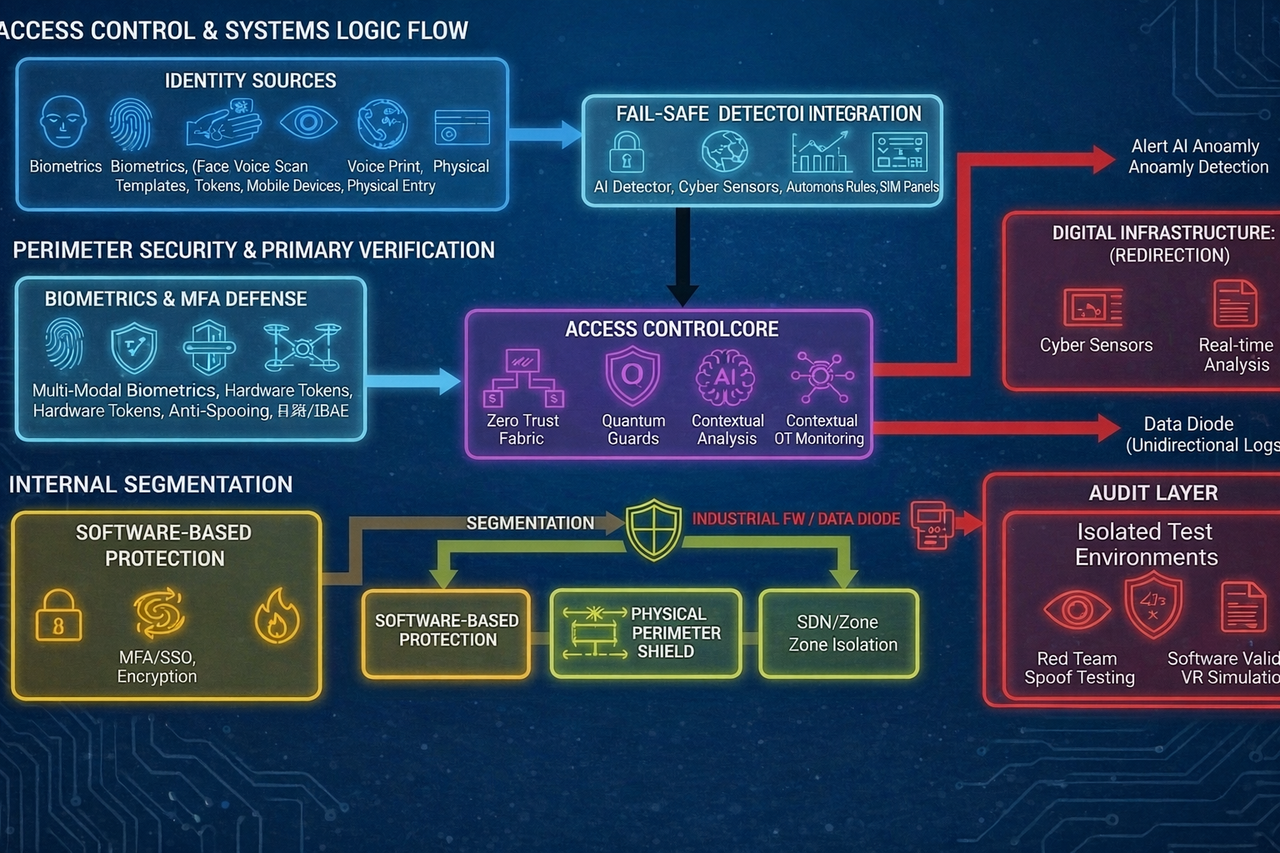
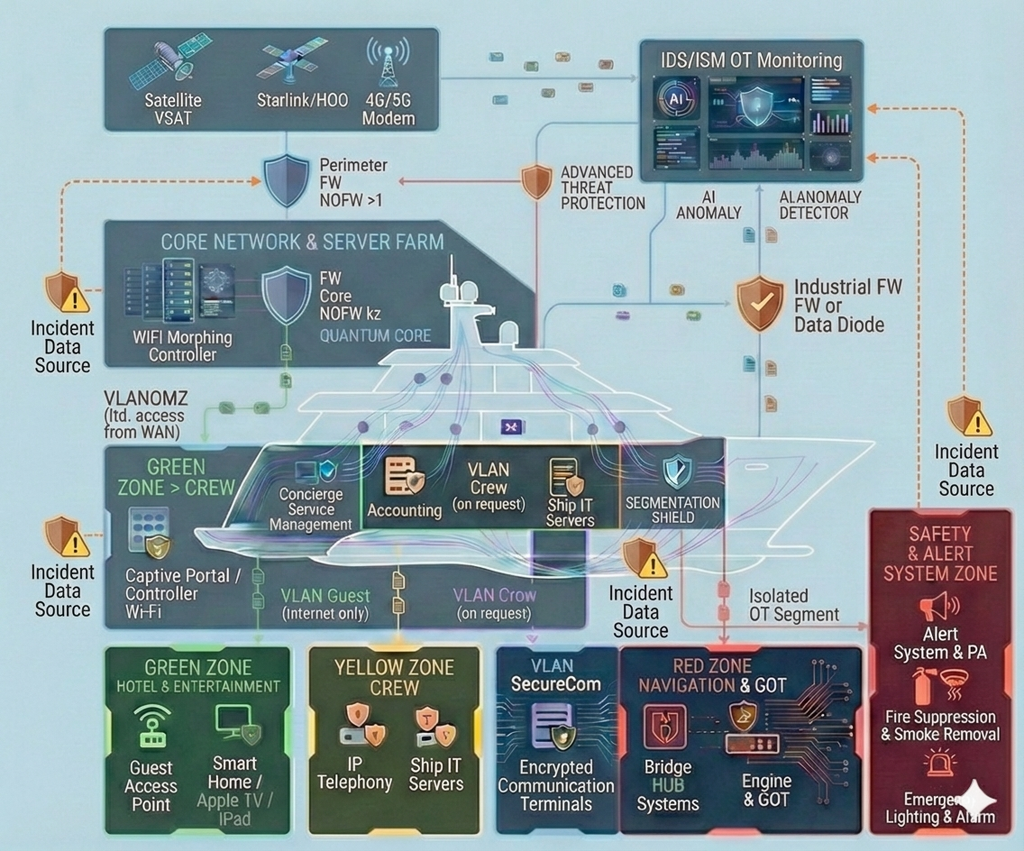
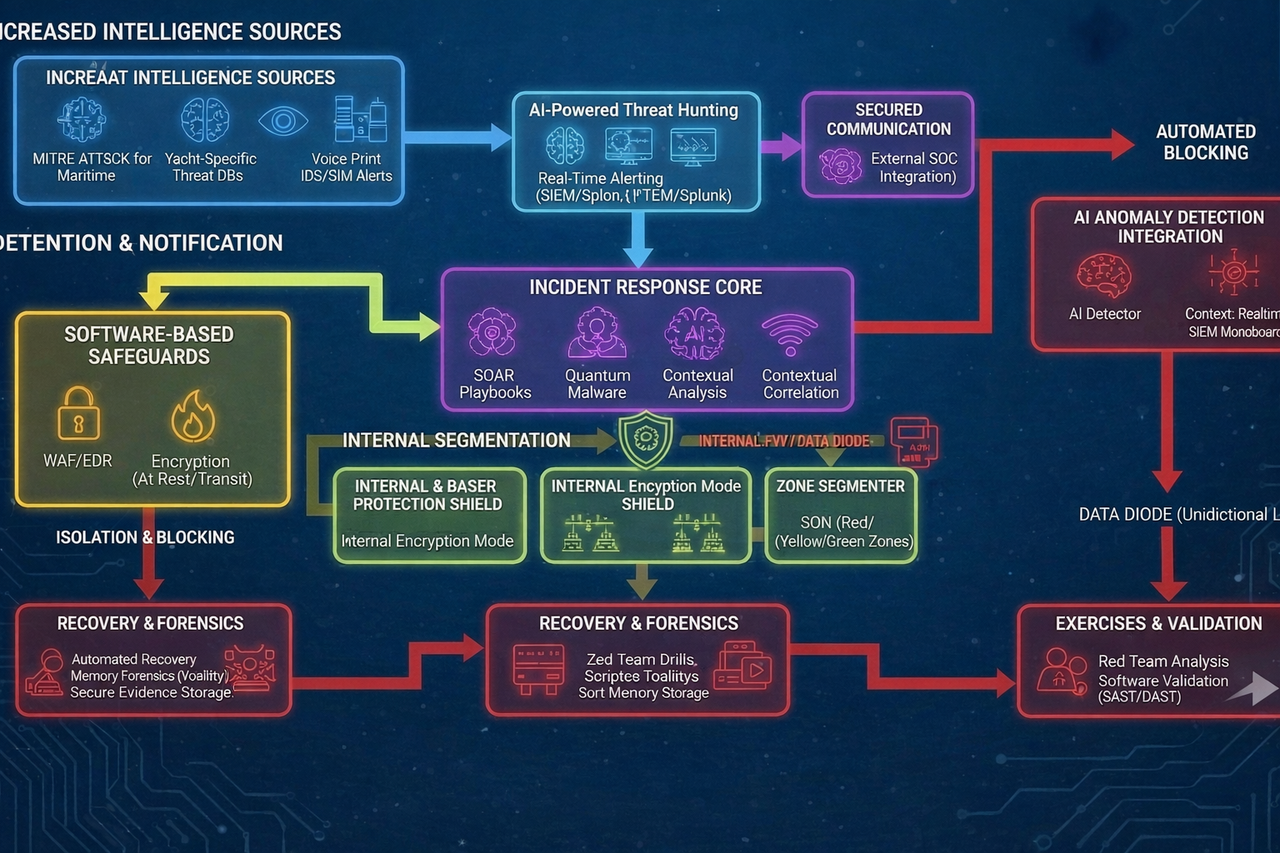
VASKOSS — Cybersecurity for yachts and maritime assets
CYBERSECURITY
safeguarding business interests
A maritime vessel is critical infrastructure; large yachts are its most technology-dense and most exposed class
While traditional IT support focuses on routine technical tasks, we safeguard your maritime operations from cyber risks that can cause financial, reputational, navigational, and physical safety impacts
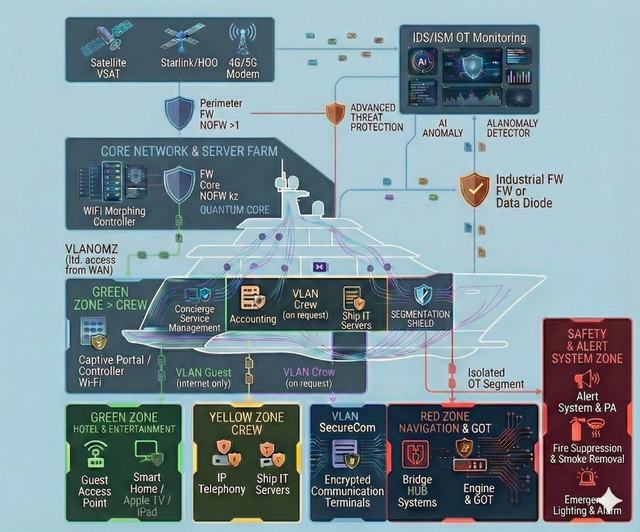
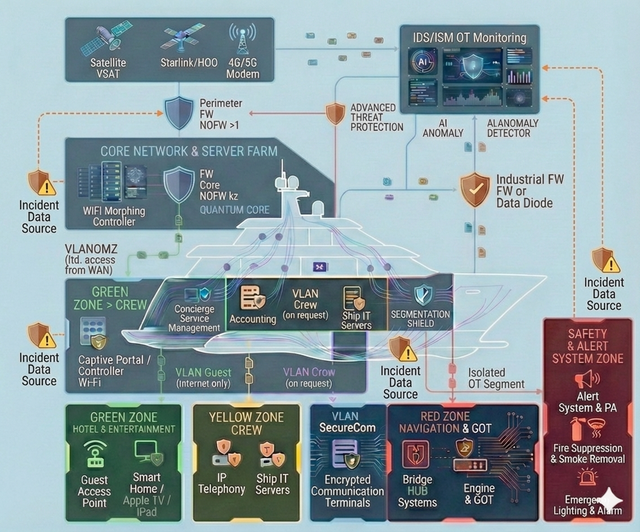
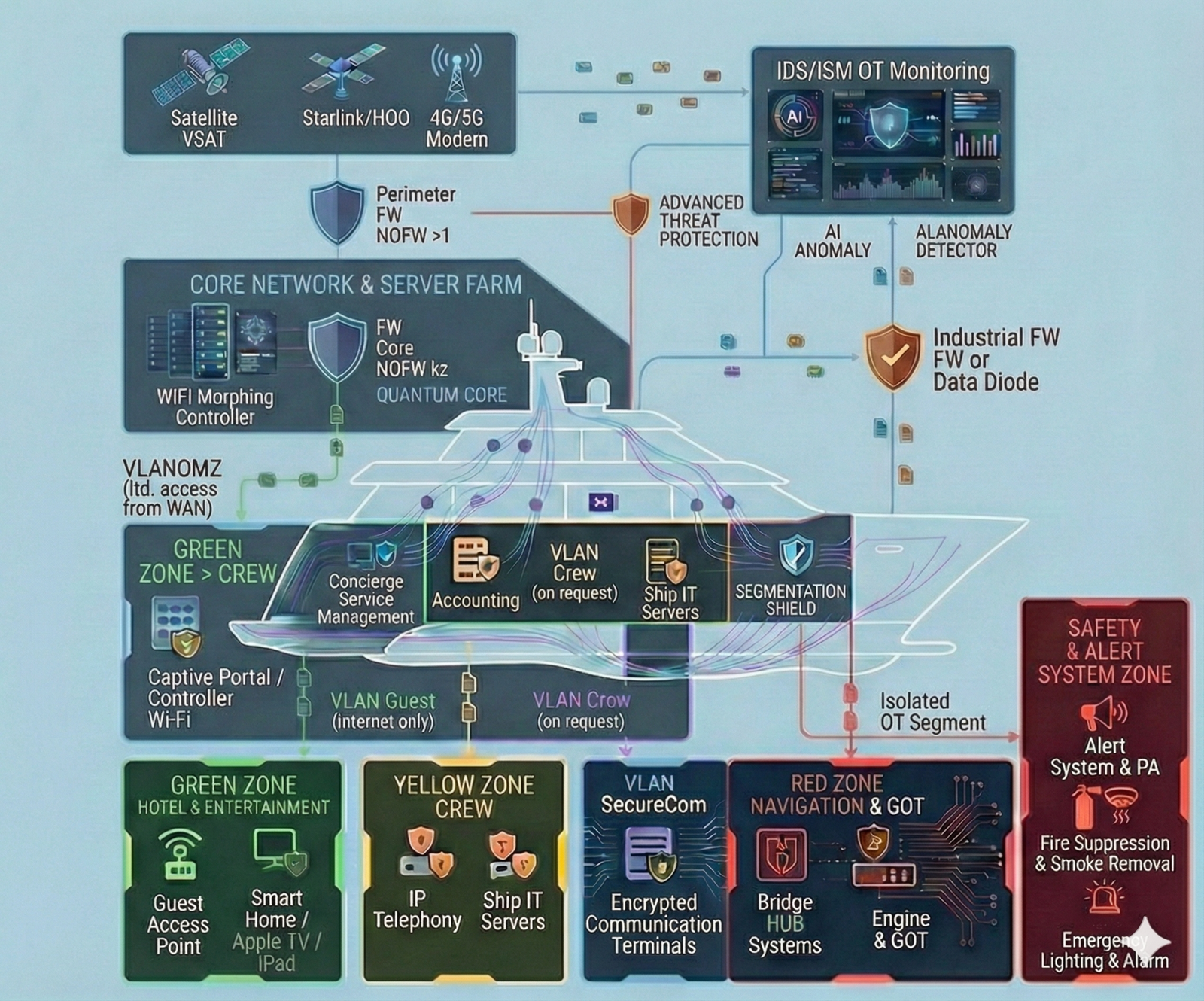
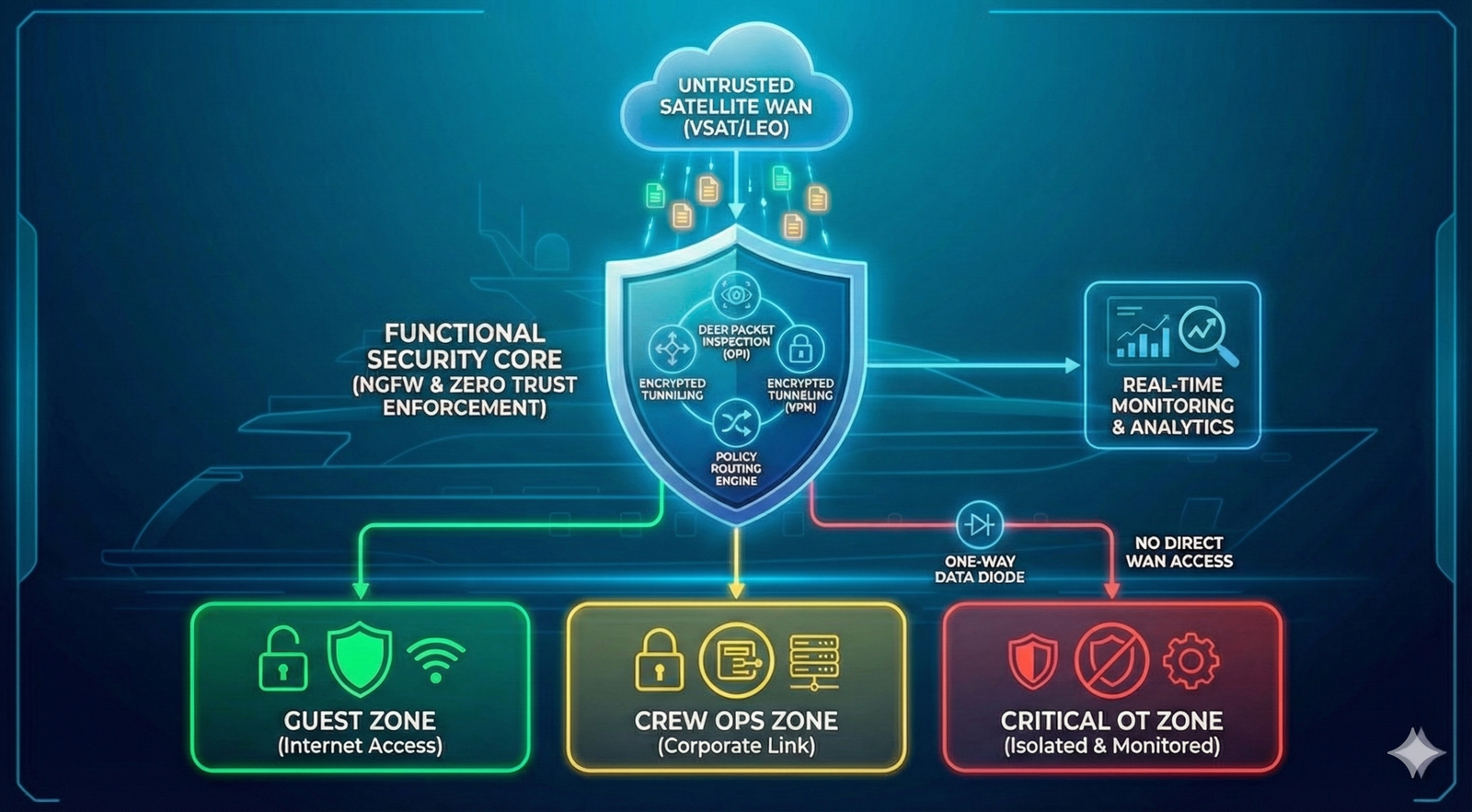
Navigation Disruption (OT)
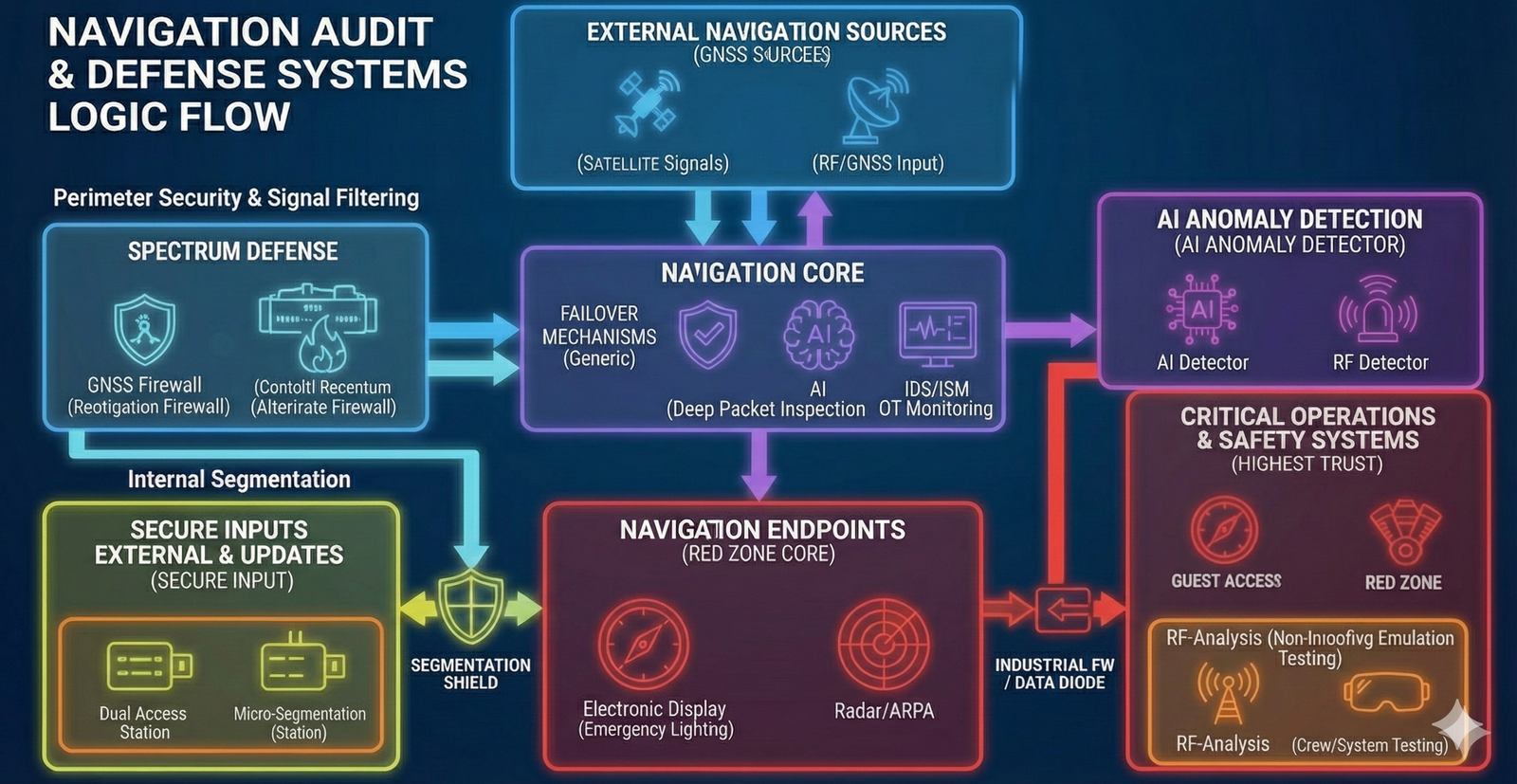
Interference with GPS, ECDIS, or engine propulsion control/monitoring systems may compromise the integrity of navigation data, distort the displayed situational picture, and/or enable unauthorized changes to control parameters. This increases the risk of loss of vessel control, deviation from the intended course, and a navigational incident—potentially escalating to collision or grounding.
Corporate Espionage
Unauthorized interception and eavesdropping on the owner’s and key personnel’s confidential business communications via compromised network infrastructure and insufficiently secured communication channels (including VoIP and messaging platforms), with the intent to obtain commercially sensitive information.
Cyber Incident Unpreparedness
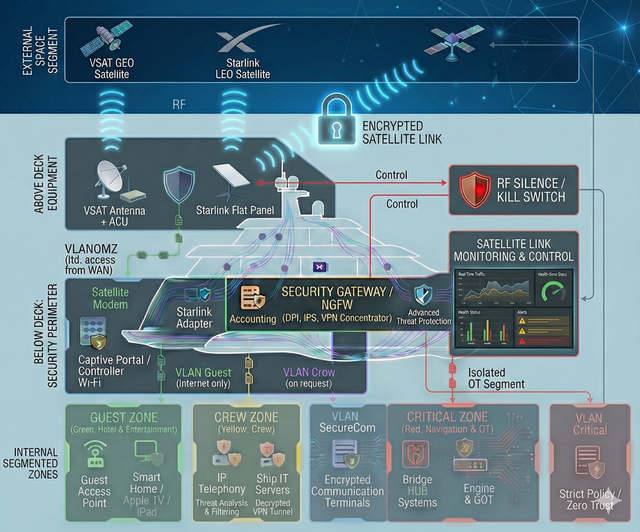
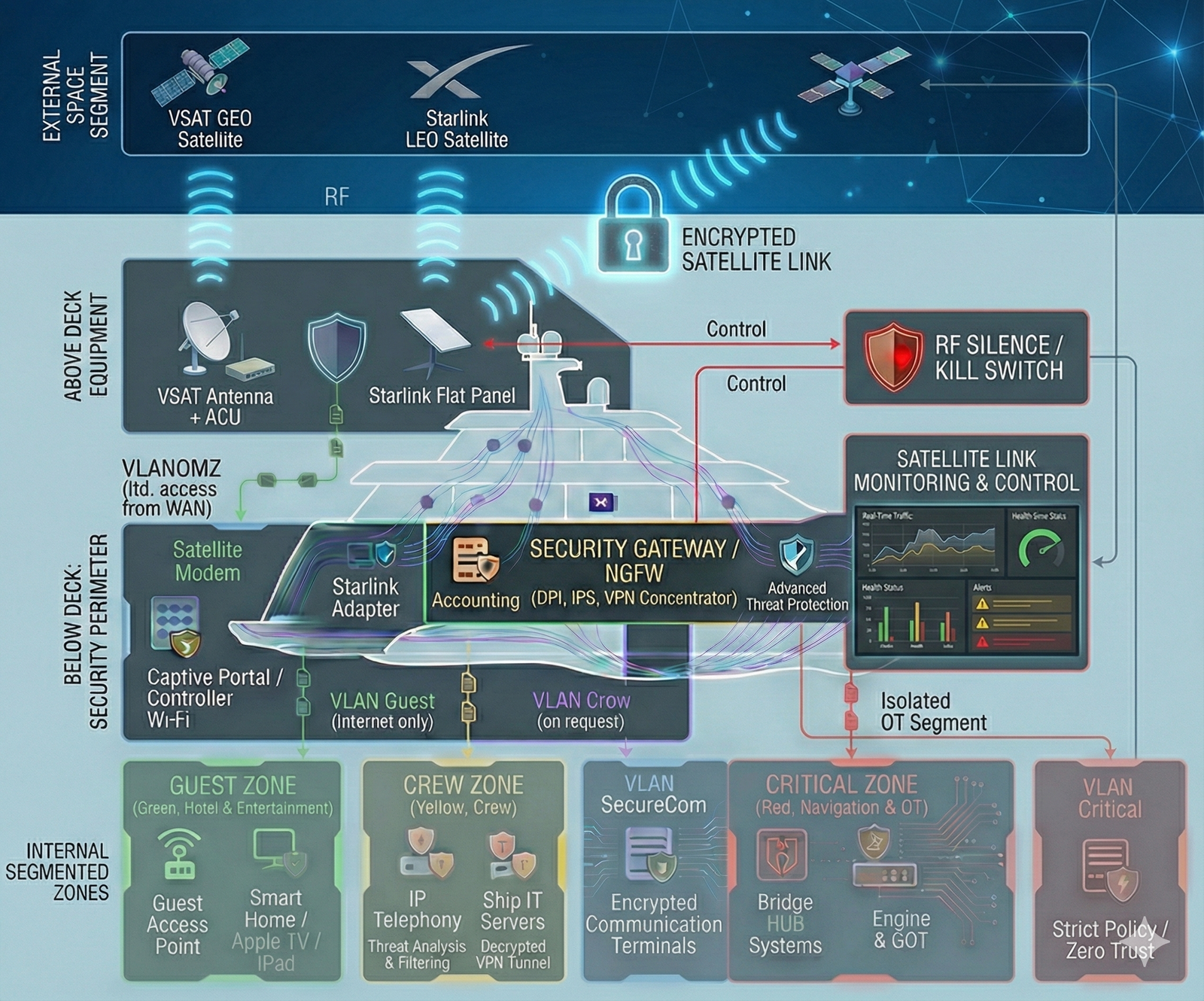
The absence of a formalized incident response and recovery plan (Incident Response / Business Continuity) and clear role assignments during an attack, resulting in uncoordinated actions by the crew and staff. This is particularly critical in cases of satellite connectivity compromise (e.g., Starlink) or onboard network disruption/degradation, leading to service downtime, loss of communications, and prolonged recovery time.
Critical Infrastructure Protection Standards
With expertise built since 2004, we deliver reliability trusted in high-risk and highly confidential environments
Privacy Protection
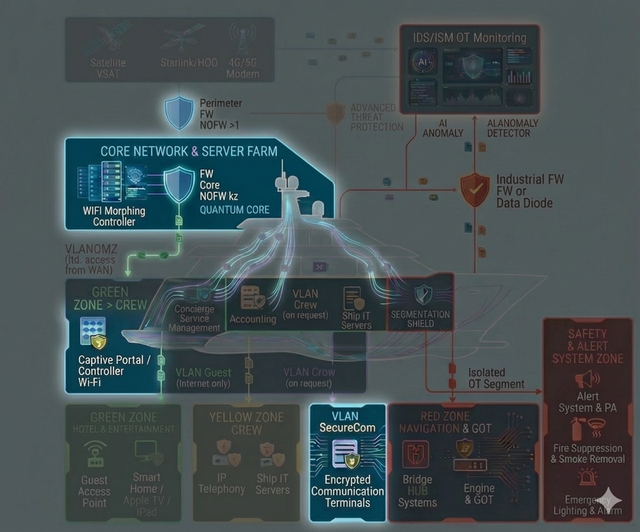
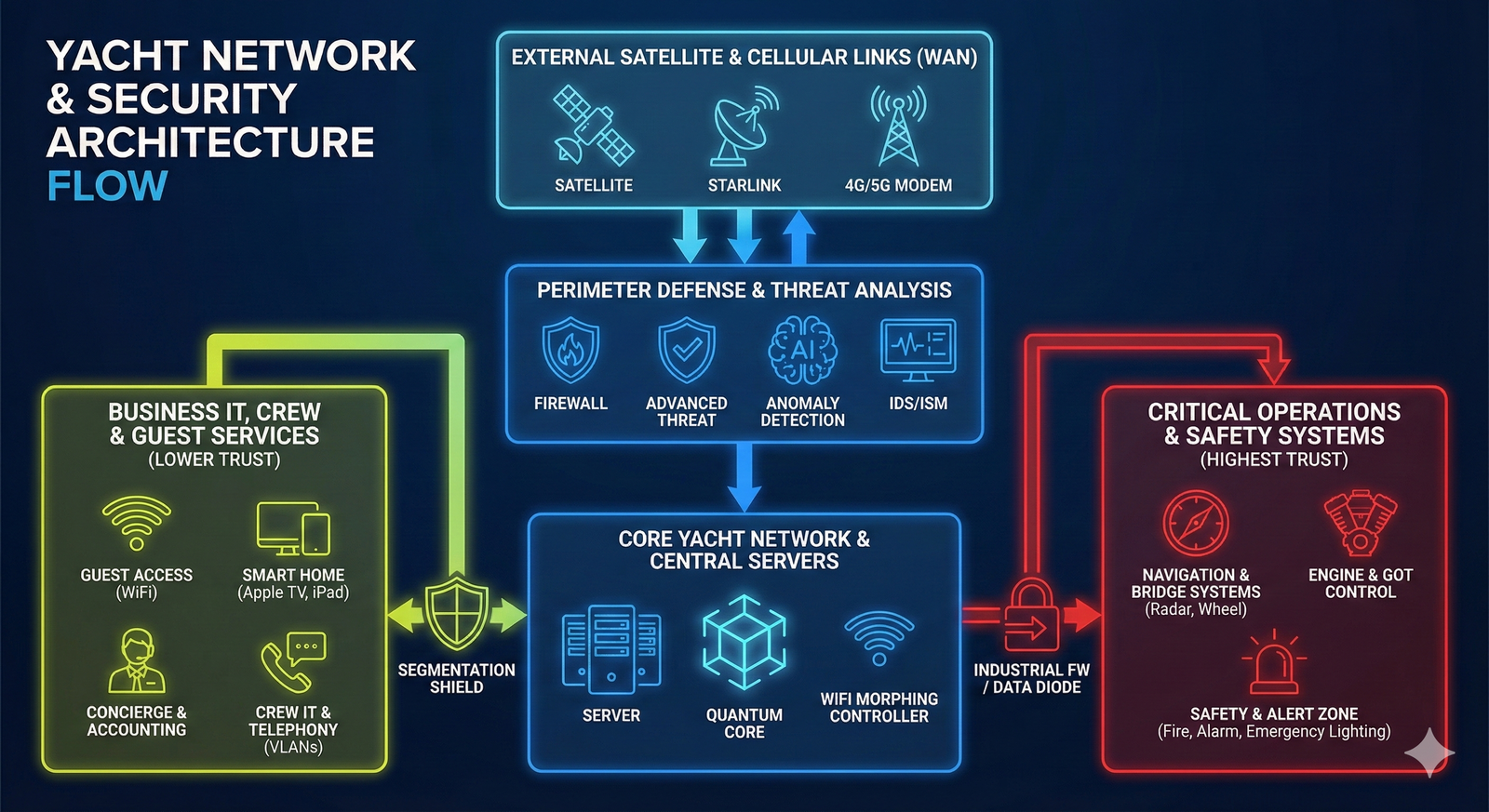
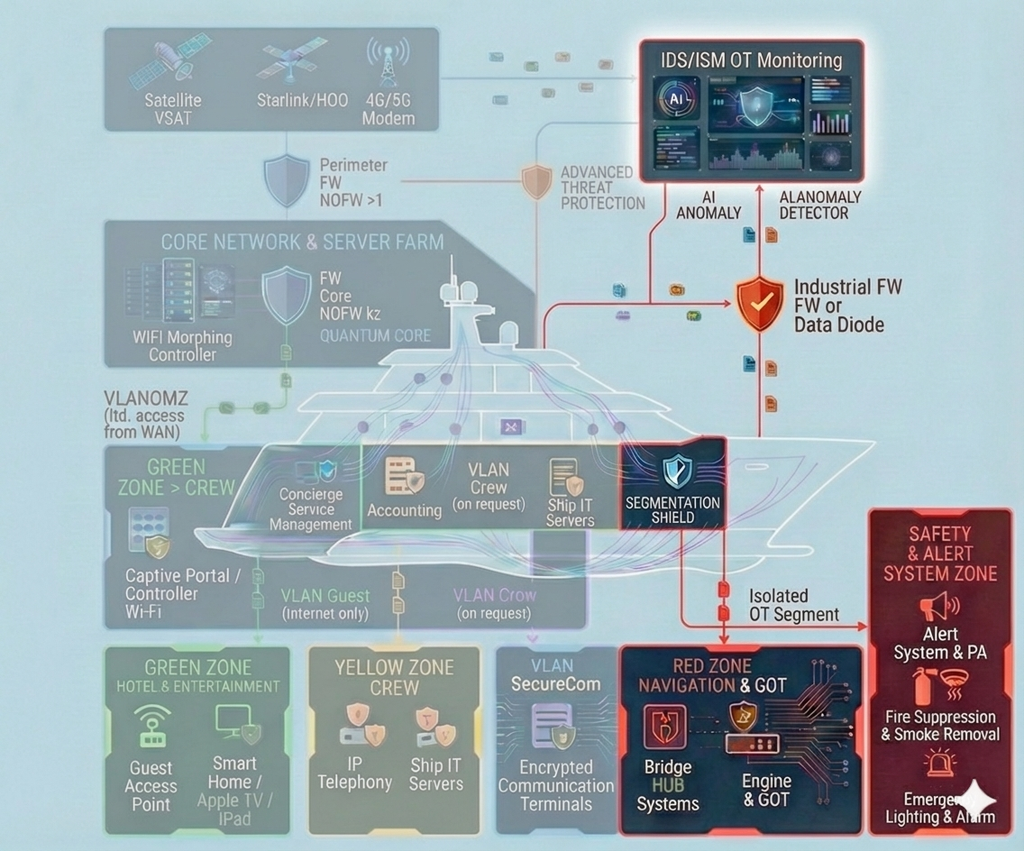
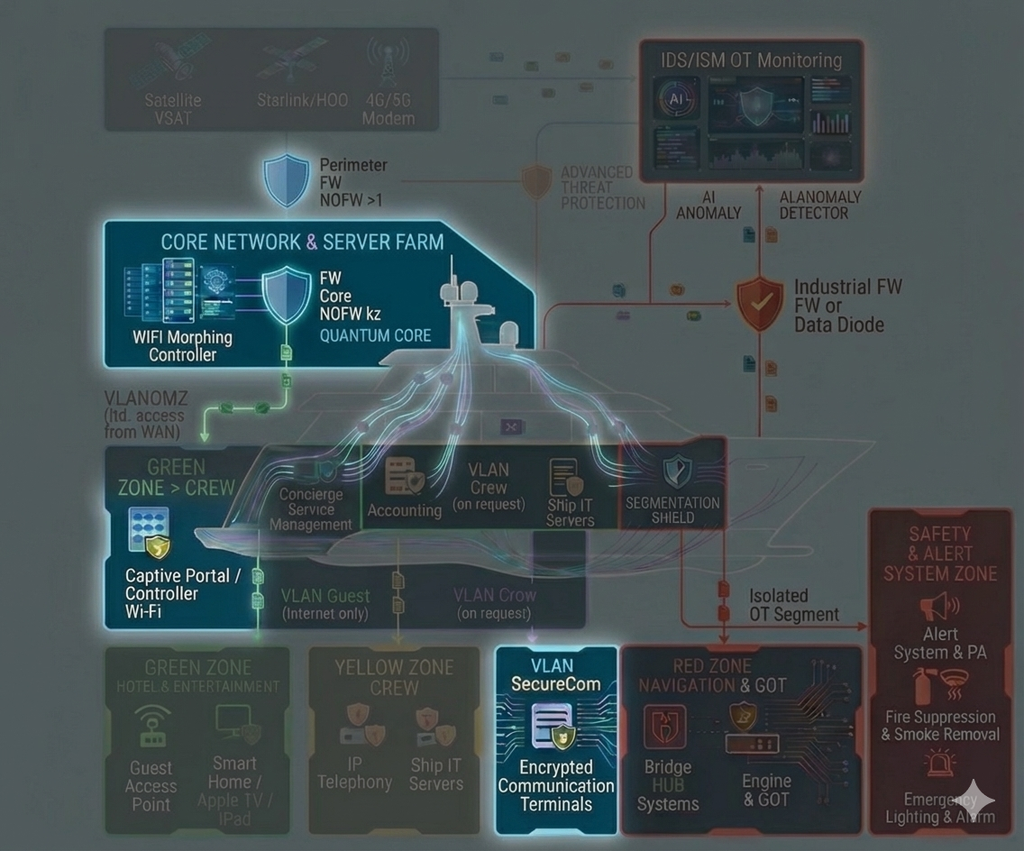
We establish segmented “Clean Zones” onboard—isolated digital enclaves with strictly controlled access, designed for navigation systems and confidential communications. The architecture and protective controls are implemented in line with the most stringent cybersecurity practices, typically applied to safeguarding highly sensitive information and trade secrets, minimizing the risk of data leakage and unauthorized interference with the yacht’s critical systems.
Incident Response (IR)
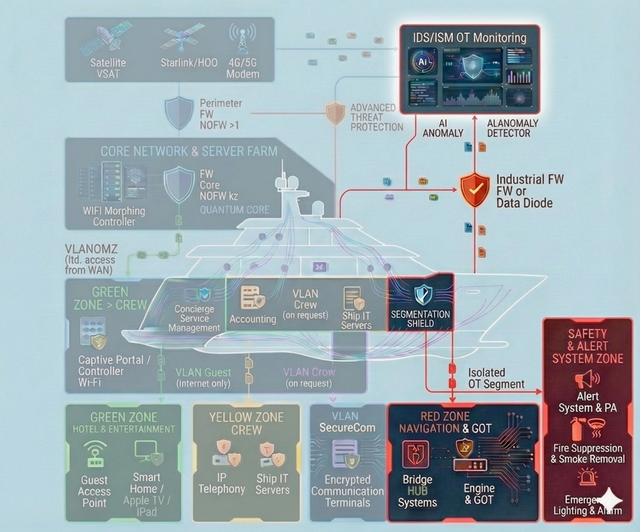
The cybersecurity system we develop provides continuous monitoring and early detection of incidents, their rapid isolation and containment, as well as effective response and remediation. As part of the work, we perform the collection and analysis of digital artifacts (digital forensics), enabling us to quickly determine the root cause and attack vector, preserve the evidentiary trail, and ensure a controlled restoration of system operations in the shortest possible time.
Practical Compliance
We prepare seagoing vessels for certification in line with IACS/IMO requirements, achieving practical, evidence-based compliance through the implementation of technical and organizational cybersecurity controls, improved resilience and fault tolerance of critical systems, and well-rehearsed incident response procedures — with a focus on real operational safety rather than merely “closing” documentation items. At the same time, we treat large yachts as a distinct, more demanding profile: higher IT/OT density, extensive system integration for comfort and connectivity, and elevated expectations for privacy and uninterrupted operations — therefore controls and verification are deeper, and threat and response scenarios are tailored to the yacht environment.
Technical Expertise
Services
Special Offer
We capture your shipboard IT/OT infrastructure and cybersecurity perimeter as-is in a Digital Technical Passport for Shipboard IT & Cybersecurity Systems — with no operational disruption and no systems taken offline. We consolidate and structure asset inventory, configurations, versions, documentation, and ownership/accountability, and establish baseline controls and procedures — so the crew and shore organization always have an up-to-date, connected, and auditable single source of truth. Delivery format: a dedicated Private SaaS platform with secure VPN access — a continuously maintained technical record for the shipowner, the master, and the shore organization.
VIP Privacy Shield
A comprehensive set of measures to protect the personal devices of key shipboard personnel (smartphones, laptops, and tablets) — from configuration hardening and integrity monitoring to secure access to onboard and shore-based services — with a focus on reducing the risk of data leakage, account compromise, and operational disruption affecting the vessel. The same approach is then extended to the personal devices of the owner, senior management, and passengers/guests (depending on vessel type and voyage profile): encrypted and authenticated communication channels for confidential conversations, plus detection and neutralization of digital surveillance (traffic interception, tracking, and compromise of accounts and devices). The solution is applicable across the commercial fleet (masters, officers, technical staff, shore-based managers) as well as large yachts, where privacy and personal security requirements are typically more stringent.
Navigation & OT-Security
Segmentation and strict isolation of critical onboard systems — with dedicated protected zones for navigation (including ECDIS) and for propulsion/engine control and monitoring — so that incidents in guest, office, or service networks cannot propagate into the critical domain and impact the vessel’s safe operation. In addition, we implement measures against GPS spoofing and manipulation of navigational data (anomaly detection and integrity checks on input data), and establish centralized control and audit of remote access to engine-room systems: a single controlled entry point, logging, MFA, and the principle of least privilege. The approach is applicable to the commercial fleet as well as large yachts, where stricter contractor isolation and increased attention to risks related to satellite communications and the onboard network are typically required.
24/7 Monitoring & Response
Continuous security monitoring of systems and security events with early incident detection, rapid isolation and containment, and remediation. Includes Digital Forensics to identify the root cause and attack vector, preserve the evidentiary trail, and enable accelerated, controlled restoration of operations.
Pre-Compliance & Crew Training
Preparation of maritime vessels for inspections and IACS/IMO requirements with practical readiness ensured: design and implementation of a cyber risk management system (policies, roles, procedures, technical controls), crew training for cyber-incident response and resistance to phishing/social engineering, and support for the design and continuous development of cybersecurity throughout the vessel lifecycle. For large yachts, we additionally strengthen the privacy perimeter and governance of external integrations: control of contractors and integrators during newbuild, refit/modernization and maintenance, including secure supply and configuration requirements, access management, logging, acceptance testing and compliance validation.
How to Start
Confidential Initiation & NDA
Contact us to outline your objectives. We ensure complete anonymity, sign a Non-Disclosure Agreement (NDA), and gather initial data. Your privacy is secured from the very first interaction.
Inventory, Audit & Gap Analysis
We conduct a comprehensive digital inventory of your IT/OT infrastructure and assess the crew’s organizational procedures. This stage goes beyond simple checks; we map all assets, identify gaps in IACS/IMO compliance, and pinpoint vulnerabilities to build the foundation for your security documentation.
Digital Technical Passport & Remediation Roadmap
Based on the audit, we generate the vessel’s Digital Technical Passport for Information Security Systems. You receive more than a report; you get a structured asset document and a prioritized Roadmap for eliminating vulnerabilities, optimized for both security and budget efficiency.
Contact Us
Ready to discuss the cybersecurity of your vessel? Contact us to arrange a confidential consultation
Contact initiation
To comply with security and confidentiality protocols, initial consultations are conducted exclusively in writing. This ensures accuracy of technical details and creates a protected audit trail of your request.
Email: info@vaskoss.com
— for official requests and documentation.
WhatsApp: +306946880923
— a secure channel for quick text messages.
Telegram: +306946880923
— a secure channel for quick text messages.
Address: Piraeus, Maritime Hub, Greece (available worldwide).